The use of wireless . technology is increasing rapidly in critical societal functions such as energy production, transport, logistics, banking and financial systems, and industrial and security applications – this despite the fact that civilian consumer wireless technology in general is very sensitive to both unintentional and intentional interference signals. Therefore Electromagnetic Compatibility (EMC) issues are highly important to address. Hitherto only military actors have been able to utilize or take advantage of this sensitivity effectively, but this ability is now spreading to civilian actors, thanks to sophisticated jamming equipment which is now sold openly and inexpensively via the Internet.
In this paper, the requirements on and the special threats against wireless solutions for security and safety applications are discussed and described. We show a numerical example of the vulnerability of Global System for Mobile Communications – Railway (GSM-R) to a generic low-power interference source. Finally, we describe important challenges needed to be solved to provide robustness and reliability for critical services in wireless security & safety applications.
Introduction
The use of wireless technology has exploded in recent decades and has led to most individuals today using such technology in some form. Today there are almost as many mobile subscriptions as there are people on the earth. However, not only is the use of wireless technologies increasing among individuals; it is also a general trend in other parts of the society, such as security and safety [1-3] and machine-to-machine (M2M) [4].
We can also see rapidly increasing use of wireless technologies in critical societal functions such as energy production, transport, logistics, banking and financial systems, and industrial and security applications. Within industry, wireless technologies are increasingly used for monitoring and real-time control of processes and machines. Wireless technology is also common in various types of alarm systems, such as burglar alarms, shoplifting alarms and alarm systems for cash in transit (CIT). In both aviation and maritime applications, wireless technologies are used for voice communications, identification, navigation and surveillance.
For some activities, wireless technology is a necessity. In military operations, reliable wireless technology is a prerequisite for success. Similarly, wireless technology is often a key factor in the work of police, rescue and medical personnel. There are several examples of the very serious consequences of radio communications being disturbed in such settings. As an example, this issue came to the forefront in April 2008, when two firefighters in Cincinnati died in a blaze on Squirrel’s Nest Lane. A review of the radio calls made during the fire showed that the firefighters repeatedly made mayday calls which were never transmitted. The International Association of Fire Chiefs has released an interim report [10] concerning possible communications problems involving digital two-way portable radios in close proximity to common fire-ground noise.
Another example of the importance of robust wireless communications comes from the terrorist attack in Norway on 22 July 2011. Public media report that the new TETRA based digital radio system for first responders did not have sufficient coverage at Utöya, so the district police used the older non-encrypted analog system. The elite Delta unit, dispatched to tackle the gunman, and paramedics had switched to a new, secure digital network. The consequence was that the operation was delayed since police commanders had to contact different units via email and even fax, as the mobile network was down. It was down due to overload because too many people were trying to call from their mobile phones.
During the Gothenburg riots in 2001, the demonstrators caused interference in the police radio system. This interference contributed to the chaotic situation that arose, and led to prosecution for gross sabotage. Another important example of vital wireless technology is the Global Positioning System (GPS) which is used for both navigation and positioning of personnel and units, as well as sending an accurate time signal to telecommunications networks. One example is using the GPS signal to ensure that the world’s stock markets have common time so that no operator using automatic electronic trading (robot trading) can take advantage of the time signal differing between two stock markets. GPS receivers, however, are very easy to disturb because the power in the received satellite signal is very low. This, combined with the rapidly increasing dependence on GPS in critical security applications, opens up great vulnerability to intentional interference transmission [11].
Wireless solutions are always vulnerable to electromagnetic interference and is therefore vulnerable both to unintentional and intentional electromagnetic interference. Therefore Electromagnetic Compatibility (EMC) issues are highly important to address for such systems. Unintentional interference is produced from all kinds of electronic devices and is typical a problem in dense areas such as urban- and industrial areas [4][16]. In intentional jamming, the wireless system can be attacked on distance from the receiver. No access to the physical area at the receiver is needed for such electronic attack. The purpose with such attack could be several, e.g.
- Jamming with the purpose to disrupt the transmission,
- Eavesdropping with the purpose to get critical information from the transmission,
- Spoofing with the purpose to manipulate the receiver with false information.
Jamming of police radio systems began to happen in the early 2000s in connection with demonstrations and riots. Examples of this being highlighted in the media occurred at the World Bank meeting in Prague in 2000, at the EU summit in 2001 (the Gothenburg riots) and at the riots in Sydney (Cronulla and Brighton le Sands) in 2005. At these events either pure jamming and/or transmission of false calls were used to cause confusion in the police operations. International media regularly reports jamming being used in connection with theft and burglary. A common target is alarm systems that use wireless technology.
Examples of alarm systems subjected to jamming are shoplifting alarms and burglar alarms, home alarms and assault alarms for CIT and limousines. Jamming of GPS receivers has been reported for a variety of GPS applications. This includes, for example, GPS receivers used to track valuable cargo or to register routes for various commercial vehicles. Near North Korea’s borders numerous cases of jamming against airborne GPS receivers have been reported. Furthermore, jammers are also used to block wireless locks in cars so that the car is not locked when the owner presses his wireless key. This technique is typically used in large car parks, and means that the owner does not notice that the car is unlocked. When the owner has left the car, it is emptied of valuables. The growing presence of jammers in itself increases the risk of pure accidents if the jammers accidentally knock out vital systems.
One example is from Newark Airport in New Jersey in 2009, where several of the airport’s GPS receivers were being knocked out at regular intervals. After a long investigation, it turned out that it was a passing lorry that had disrupted the GPS receivers. The lorry driver had installed a GPS jammer to jam the GPS receiver that the employer used to log drivers’ routes. After that incident, a detection system has been used. In 2013, a truck driver was caught in that area and was fined $31,875 for using such GPS-jammer. The detection system has continued to experience regular interference from GPS jamming approximately five events per day mostly Monday to Friday [13]. The problem seems to be widely spread, which is also supported by the Sentinel study in UK that has recorded more than 60 jamming incidents in six month at one location and the researchers estimate that there might be up to 450 GPS jamming occurrences in UK every day [12].
In military operations, it has always been a well-known fact that effective wireless communication is a prerequisite for command and control. For this reason, radio interference is an established and well-known method of effectively reducing an opponent’s ability to lead his units. Historically, tactical jamming of the radio has been, with few exceptions, a purely military capability.
Today, this ability has started to spread among illegal actors in society, which means a rapidly growing threat to critical wireless communications, for example, police, rescue services, wireless alarm and surveillance systems. The ability is spreading as jamming equipment is now sold at low cost via the Internet, see Figure 1.

The fact that the use and possession of jammers is prohibited in many countries has not stopped the market for these growing rapidly in recent years. A player who wants to use jamming can already for a few hundred dollars buy a jamming device adapted to any existing civilian wireless system. So far, the ability to use these jammers has been limited to single events during riots and theft. However, evidence suggests that the ability is evolving towards continued increased understanding of how this technology can be used, well synchronised with other activities at more advanced operations and more complex targets.
Eavesdropping was a problem for analog emergency operations since activists and criminals could follow e.g. the police´s communications. This was prevented when the digital TETRA standard was developed and where encryption is used. Even in public mobile networks such as GSM and 3G, well encrypted services have been developed, mainly as a requirement for e-commerce and payments directly via the mobile terminal. The AIS (Automatic Identification System) is the automatic tracking system used on ships and by vessel traffic services (VTS) for identifying and locating vessels by electronically exchanging data with other nearby ships, AIS base stations, and satellites. Information, such as unique identification, position, course, and speed, is openly transmitted and is public available. This might be a problem since it is possible even for criminals and terrorists to track e.g. vessels with hazardous substances. Even the DME (Distance Measuring Equipment) which is a transponder-based radio navigation technology in air-traffic control, is a non-encrypted signal that can be used for identifying and tracking aircrafts.
Spoofing has been highlighted for e.g. AIS and GPS. Spoofing for GPS receivers has been highlighted due to that lots of critical functions are supported by either the positioning service or the GPS time signal for e.g. synchronization of telecommunication systems. A ”proof-of-concept” attack was successfully performed in 2013, when the luxury yacht ”White Rose” was misdirected with spoofed GPS signals from Monaco to the island of Rhodes by a group of mechanical engineering students from the Cockrell School of Engineering at the University of Texas in Austin. Even spoofing of the AIS system [7] has been highlighted e.g. with the purpose to hide if a vessel deliberately deviates from the expected route for some time.
The paper is organized as follows. In the next section, we present examples of wireless technology used in security & safety applications. That section is followed by a discussion about the contradiction between capacity and robustness and we show examples of the differences of these properties between systems. That section is followed by an overview of different ways of performance degradation due to jamming and interference. The important conclusion is that disruption is not the only observable performance degradation when jamming and interference is present. Examples of consequences of jamming against Global System for Mobile Communications – Railway (GSM-R) (for the European Train Control System) and IEEE 802.11p (for active road safety) are shown. In both cases, non-disruptive communications with low latency is crucial. We show that a portable jammer can cause critical problems even with a moderate output power. The next section shows a comparison between properties on civilian wireless consumer electronics and the specific needs for security & safety applications. Important challenges to address the special needs described are summarized before the paper is finally concluded.
Wireless security & safety applications
Wireless technologies in security & safety applications are continuously increasing. In Table 1, some examples of wireless technologies/standards in security & safety applications are listed. As seen, security & safety applications can be found in a large frequency span, from kHz- to GHz region.
Capacity or robustness?
A robust radio system is designed to resist higher levels of electromagnetic interference without the loss of accuracy in the information transferred. However, high robustness against interference has its price since it costs in terms of capacity in the system. With capacity we mean for instance data rate or number of users in a certain system. Robustness against interference always means that redundancy is put in the system. This redundancy steals capacity that could be used to send pure information bits. In civilian consumer wireless communication systems, capacity has in general the highest priority since as many users as possible is the overall purpose of those systems, for commercial reasons. In military & space systems however, robustness in general has the highest priority since it is of vital importance that all information reaches the end user even if hostile jamming is present. In Figure 2, this is illustrated by a comparison between systems with different degree of robustness against interference.
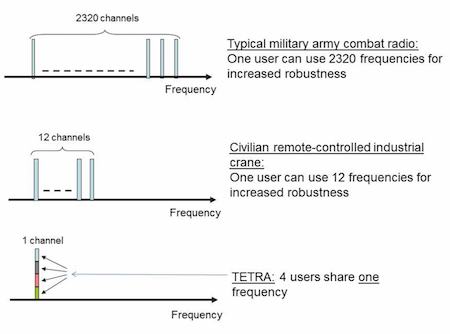
All three systems in Figure 2, need one channel for their transmission needs. The military system can typically use up to 2320 channels in the 30–88 MHz band only for increasing the robustness against jamming. The radio system for remote-control of a factory crane typically can use up to 12 channels for increased robustness. In a TETRA-system, however, four users typically share one single channel. As an example, if a military radio uses all available channels in the 30-88 MHz frequency band, a jammer would have to increase its power with approximately 33 dB in order to ensure the same interference impact as on a TETRA channel. For wireless communications in critical security & safety applications, it is of vital importance to cope not only with unintentional interference from co-located electronics but also from intentional jammers.
Thus, in these applications, the requirements on the wireless systems are similar to that for military and space communications. An important conclusion from this is that if we in critical applications use products optimized for capacity and therefore with negligible robustness against interference, we have opened up for a serious vulnerability against jamming. Another example on the difference in robustness between civilian consumer products and military products are GPS. The civilian MHz. Thus, jamming a military GPS signal would in general require ten times the power than needed to jam the civilian GPS.
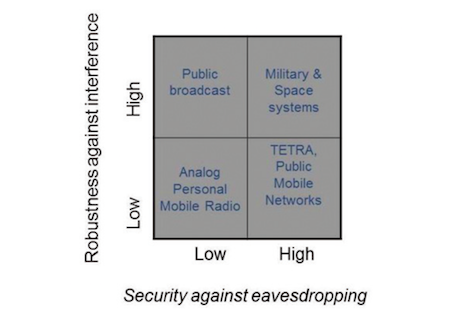
Furthermore, robustness against interference does not have anything to do with security against eavesdropping. However, this is not always fully understood by users. Encryption does not provide any robustness against interference but makes it difficult for an eavesdropper to obtain information from the signal. In Figure 3 we show examples of how robustness against interference and security against eavesdropping differs between some standards and applications. In general, military and space systems are designed to have an inherent robustness against interference. Furthermore, public broadcast services, as e.g. public radio stations, are also robust to interference due to its high transmission power and good antenna conditions. Both TETRA and public mobile networks (e.g. GSM, 3G, 4G) are well encrypted but are vulnerable to intentional jamming, see e.g. [15][16]. When the TETRA standard was developed in the 1990´s, encryption was prioritized and not robustness against jamming. At that time, the threat from intentional jamming was not present but has increased the last 10-15 years due to the increased availability of efficient low-cost jammers sold on the Internet.
Performance degradation due to electromagnetic interference
EMC problems in wireless systems can result in a variety of symptoms for the user. The most obvious impact of jamming and unintentional interference may be disruption in the wireless system. In that case, the user gets a clear sign that a problem has occurred. However, disruption is not always the most common sign of that interference and/or jamming is present. Depending on the system of interest different more or less diffuse consequences can occur such as
- Reduced communication range
- Lost calls/messages
- Latency of data
- Reduced number of users in networks
- Position errors (GPS)
- Increased sensitivity to electronic attack (increased range for jammers)
- Shorter detection range for warning systems
Hence, the appearance of jamming and interference is often difficult to recognize. If one user exhibits lots of interference, incoming calls will not be registered. However, outgoing calls from that user will function as usual. In that situation the communication will work in one direction which will probably cause confusion. In some systems, such as wireless local area networks (W-LAN) an increased amount of interference results in time delays and slower data rates. In a GPS receiver, interference can cause either disruption or an increased position error, depending on the specific receiver design.
First responders report to the authors that the shift from analog to digital radio systems has one major practical drawback with respect to unpredictable communication problems. In older analog systems it was possible to, on an early stage, experience an emerging communication problem since the analog device in general has a rather smooth transition from a state with high communication quality to a stage with low communication quality. The analog device gradually indicates to the user if interference or other reception problems are approaching. If the device is used for voice communication, the indication can typically appear as an increasing noise level. This gives the user the possibility to take actions to prevent disruption such as moving to another position.
Additionally, an aggravation property of digital systems is that the transition from high to low communication quality goes very rapidly, with no chance for the user to react with precautions because the used channel code does not give any improvement beyond a specific noise level. Therefore, disrupted communication perceives to arise more sudden for digital radio systems than for analog systems. This means that a user in practice has very limited possibilities to identify and react to communication problems. Radio terminals usually do not support the users by warnings about the upcoming communication problem. Experience has shown that unpredictable disruption of communications during emergency operations can have severe consequences both for personal safety and for the ability to conduct a successful operation. An early-warning service for emerging communication disruption due to both unintentional interference and jamming, would therefore be a significant contribution for increased safety and security in such operations. A possible solution for such an early-warning service both on the terminal and on higher system level is presented in [5].
Renaults for a generic interference source and GSM-R
To illustrate the consequence of an EMC-problem on a wireless application, an example involving a generic electromagnetic interference source is shown. GSM-R (Global System for Mobile Communications – Railway) or GSM-Railway is an international wireless communications standard for railway communication and applications. GSM-R is a sub-system of European Rail Traffic Management System (ERTMS), and is used for communication between train and railway regulation control centres. The other part of ERTMS is the European Train Control System (ETCS), which is a signaling, control and train protection system designed to replace the many incompatible safety systems currently used by European railways, especially on high-speed lines.
In ETCS, upper limits of latency are specified for Quality-of-Service. The train maintains a circuit switched digital modem connection to the train control center at all times. This modem operates with higher priority than normal users. If the modem connection is lost, the train will automatically stop. This can occur e.g. if the latency exceeds a certain limit or the transmission is disrupted for a certain amount of time. Such feature makes the system vulnerable to electromagnetic interference and jamming if this will cause disruption in the GSM-R signal for a certain amount of time. Jamming against GSM-R has been studied e.g. in [8] where an overview of different jamming methods is shown together with results where the bit error rate (BER) is measured for different jammer-signal ratios and different jamming signals. In our example, we also use an analysis based on power ratios to analyze the vulnerability for a specific scenario.
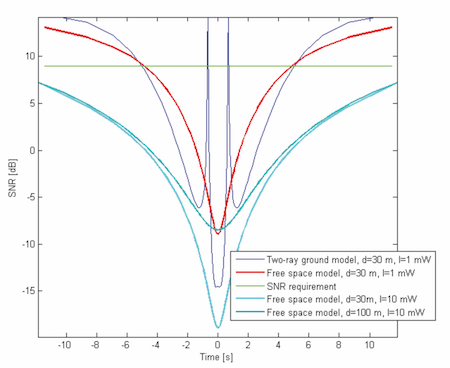
In Figure 4, we show an example of the Signal-to-Noise Ratio (SNR, here including the interference power) in a GSM-R receiver on board a train, with a velocity of 200 km/h, will be affected as a function of time when a static generic interference source is passed. The system is assumed to initially have an SNR of 15 dB before the train is interfered by the jammer. The received signal at the GSM-R receiver is assumed to -70 dBm (based on that the received power at the train antenna typically ranges between -20 dBm and -90 dBm [8]. The time value 0 s denotes the moment when the train passes the jammer at the shortest distance d. The interference source is assumed to have an output power I of 1 or 10 mW and has an omnidirectional radiation pattern. In the figure, the SNR requirement of 9 dB is inserted [14].
In [6], a maximum transmission interference time of 1 s is specified. The parameter specifies the maximum time the SNR of the GSM-R receiver may be lower than a certain acceptable level to not violate the GSM-R service. If the SNR is lower than a certain limit, the result will in practice be as if the link is disrupted or lost. In the figure, the blue curve shows the resulting SNR when also considering the influence of ground reflection (two-ray ground model, assuming antenna heights of 2 and 4 m, respectively) as an example. The figure shows that there is a substantial risk for service outage even for low-power interference sources at rather short distances and that the results are not particularly dependent on the assumed channel models. The figure shows that in such scenario, the link could appear as disrupted for up to 20 seconds.
Other applications with critical time requirements are active road safety services based on the IEEE 802.11p standard intended for vehicle to vehicle/infrastructure (V2X) communication. Most active road safety applications have a requirement on maximum delay of 100 ms [10] to ensure that the information is still valid in such mobile scenarios. As the system standard is based on carrier sense multiple access (CSMA) and also uses automatic repeat request (ARQ), there is a great risk for delays, especially in harsh environments with many users.
Product properties versus needs
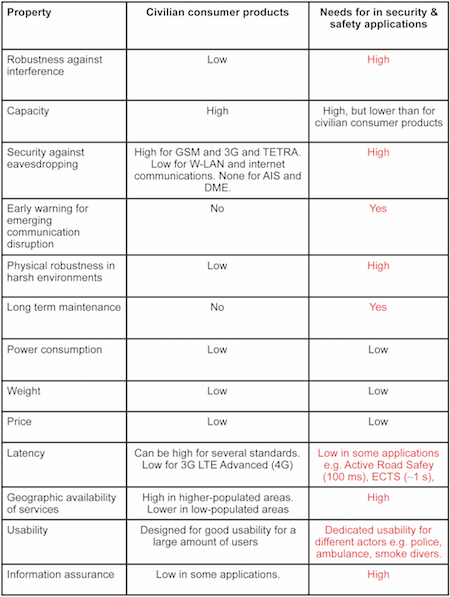
We have seen that robustness against interference is in general not prioritized in typical civilian consumer wireless products. There is however other important needs that have to be fulfilled for wireless solutions in security & safety applications. In Table 2, we show other properties and how these can be fulfilled by civilian consumer products. As seen, some needs are fulfilled and some needs are not (indicated by red text color in the table). There are several special needs for security & safety applications that are not met by consumer products so here is the challenge to meet these requirements without increasing the cost tremendously.
Challenges
Wireless communications are in general sensitive to both unintentional and intentional electromagnetic interference. Therefore, the EMC challenges are important to consider in an early phase of development or procurement. This is highly important in security and safety applications since malfunctions can have severe consequences for both people and materiel. From the discussions above, we can summarize some important challenges:
- address service-critical properties such as latency, robustness against interference, physical robustness, early warning for emerging communication problems, and information assurance regarding resistance to cyber attacks, within reasonable cost of money, and…
- provide geographic availability of services for consumer products used in security & safety applications.
Without fulfilling these properties, the communication services cannot be assured and the consequences can be devastating for security & safety services. Other properties that are important to address are:
- security against eavesdropping
- establish long-term maintenance for consumer products that are used in security & safety applications,
- provide usability in terms of human-machine interface adapted to the special conditions for security- and safety personnel.
Conclusions
A continued increase in the use of interference-sensitive wireless technology in critical societal functions dramatically increases the vulnerability to both accidental (unintentional) and intentional interference. As the ability to use jamming is increasing among civilian actors, this is important to consider over the next few years in all situations where wireless technologies are being considered for critical societal functions. This development calls for several challenges in the research and development of more robust wireless solutions. Standard consumer wireless products can be used for non-critical functions in security and safety applications. However, for critical functions there is a need for more robust solutions not to get a very vulnerable society with respect to electromagnetic interference.
Peter Stenumgaard and Kia Wiklundh Swedish Defence Research Agency
References
[1] Baldini, G., Karanasios, S., Allen, D., and Vergari, F.: ‘Survey of Wireless Communication Technologies for Public Safety’, IEEE Communications Surveys & Tutorials, vol.16, no. 2, pp. 619-641, Second Quarter 2014.
[2] Ferrus, R., Sallent, O., Baldini, G. and Goratti, L.: ‘LTE: the technology driver for future public safety communications’, IEEE Communications Magazine, vol.51, no.10, pp.154-161, October 2013.
[3] Boccardi, F., Heath, R.W., Lozano, A., Marzetta, T.L. and Popovski, P.: ‘Five disruptive technology directions for 5G’, IEEE Communications Magazine, vol.52, no.2, pp.74-80, February 2014.
[4] Stenumgaard, P., Chilo, J., Ferrer-Coll, P., and Ängskog, P.: ‘Challenges and conditions for wireless machine-to-machine communications in industrial environments’, IEEE Communications Magazine, vol.51, no.6, pp.187-192, June 2013.
[5] Stenumgaard, P., Persson, D., Larsson, E.G., and Wiklundh, K.: ‘An early-warning service for emerging communication problems in security and safety applications’, IEEE Communications Magazine, vol.51, no.5, pp.186-192, May 2013.
[6] ETSI TR 10268, Intelligent Transport System (ITS); Vehicular Communications; Basic Set of Applications; Definition, ETSI Std. ETSI ITS Specification TR 102 638 version 1.1.1, June 2009.
[7] ‘Ship trackers ‘vulnerable to hacking’, experts warn’, BBC Technology News, 31 October 2013.
[8] Mili, S., Sodoyer, D., Deniau, V., Heddebaut, M., and Philippe, H.: ’Recognition Process of Jamming Signals Superimposed on GSM-R Radiocommunications’. Proc. of the 2013 International Symposium on Electromagnetic Compatibility (EMC Europe 2013) Brügge, Belgium, September 2-6, 2013, pp. 45-50.
[9] ITU-R M.1371-5, Technical characteristics for an automatic identification system using time-division multiple access in the VHF maritime mobile band (02/2014).
[10] International Association of Fire Chiefs [2008]. Interim Report and Recommendations: Fireground Noise and Digital Radio Transmissions, http://www.iafc.org/associations/4685/wp-content/uploads/digProj_ DPWGinterimReport.pdf, Accessed June 3, 2009.
[11] ‘Global Navigation Space Systems: reliance and vulnerabilities’, Report issued by the Royal Academy of Engineering, March 2011.
[12] ‘Sentinel project research reveals UK GPS jammer use by Chris Vallance’, BBC Technology News, 22 February 2012.
[13] ‘FCC Fines Operator of GPS Jammer That Affected Newark Airport GBAS’, Inside GNSS News, August 30, 2013.
[14] Giannini, V., Craninckx, J., and Baschirotto, A.: ‘Baseband Analog Circuits for Software Defined Radio’ (Springer, 2008).
[15] Lichtman, M., Reed, J.H., Clancy, T.C., and Norton, M.:’Vulnerability of LTE to hostile interference’. Proc. IEEE Global Conference in Signal and Information Processing (GlobalSIP), 2013, pp.285-288, 3-5 Dec. 2013.
[16] Stenumgaard, P., Fors, K., and Wiklundh, K. ‘Interference Impact on LTE from Radiated Emission Limits’. Proc. IEEE EMC 2015, Dresden, Germany, Aug. 2015.


